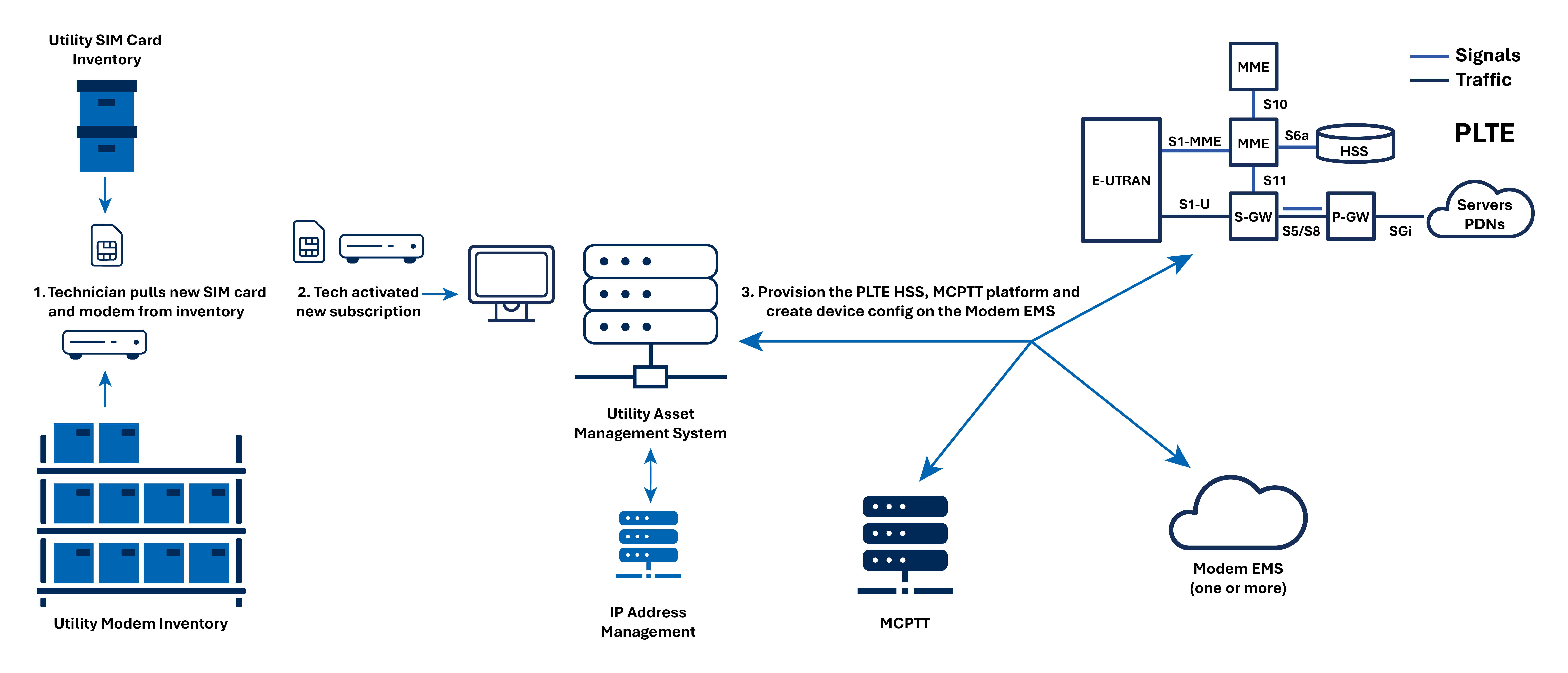
Utilities across the United States are increasingly adopting private LTE (PLTE) networks to improve the performance, security and reliability of their operational communications. With this shift comes an often overlooked but critically important technical challenge: provisioning.
To successfully scale a PLTE deployment, utilities must consider a comprehensive provisioning strategy that integrates multiple systems, supports automation and minimizes manual intervention. In creating its provisioning system strategy, a utility might have to consider whether it has dedicated technical resources available to handle the provisioning system’s deployment and ongoing maintenance. Zero-touch provisioning (ZTP) models offer a transformative opportunity for utilities seeking to scale PLTE networks efficiently and securely, but it requires careful design, given each device’s need for certain preliminary information before the device can pull its configuration over the air.