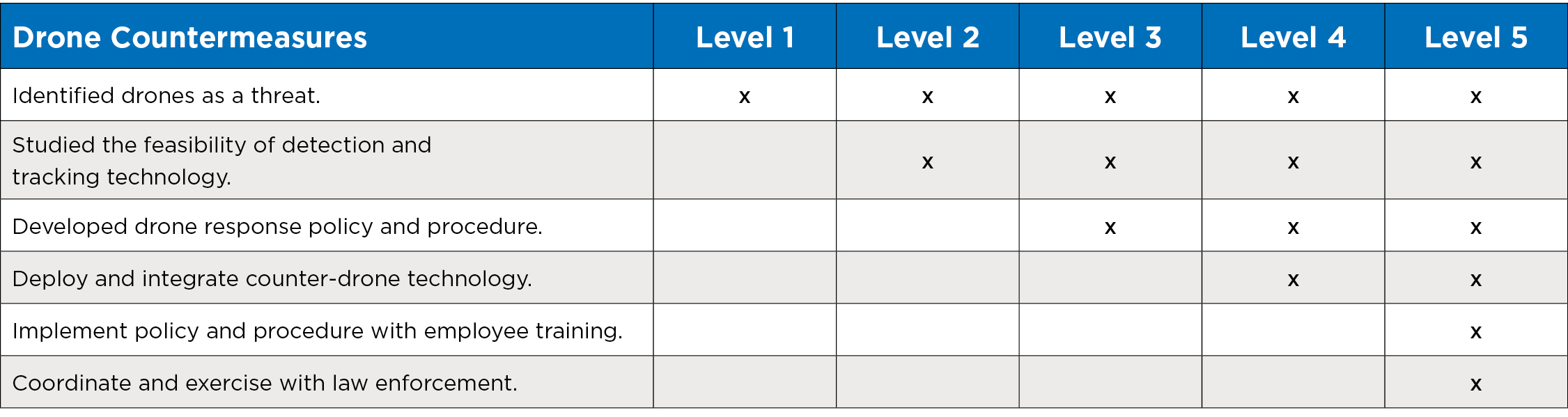
While utilities may not have as many options as they would like to for mitigating UAS attacks, proactive measures can significantly reduce the risk associated with potential drone incursions into critical infrastructure. Despite current U.S. laws prohibiting direct intervention with drones in flight, utilities can leverage a multifaceted approach to enhance defenses against UAS threats. No single solution will fully mitigate this risk, but there are several measures that can be taken to protect against UAS attacks, including:
- Deploy drone detection and tracking technology.
- Respond to drone incursions.
- Write policies and procedures for drone response.
- Coordinate with local law enforcement.
UAS Detection Technology
Utilities can procure commercially available technology to detect, monitor and track drones. Leveraging various methods including radar, acoustic, optical, infrared and radio frequency detection, this technology is a useful tool to ascertain the frequency and incidence of UAS intrusions. This information is instrumental in evaluating risks and identifying requisite counter-drone measures. Also, some technology can pinpoint the precise location of the drone pilot, a feature principally beneficial for law enforcement response. Technology using jamming, spoofing, hacking, netting, shooting or other capturing methods violates federal laws, which prohibit interference with aircraft navigation or communication systems.
Effective Response Strategies to UAS Incursions
Timely response to UAS incursions can help utilities promptly identify and rectify damage inflicted by drones. These steps can spur further investigation, if necessary. Mere awareness of a UAS incursion is insufficient to mitigate a drone attack. If a utility decides to deploy drone detection technology, timely response is essential for mitigation and deterrence.
Policies and Procedures
To improve response efforts, utilities would benefit from establishing clear roles and responsibilities to address UAS incidents. This involves establishing protocols for how and when to coordinate with law enforcement agencies, FAA officials and local authorities. Written policies and procedures can provide clarity regarding employees’ authority by identifying when police involvement is warranted and establishing incident investigation safety protocols.
Law Enforcement Response
The FAA recommends that law enforcement observe and report potential violations of federal drone laws. While local law enforcement lacks the authority to proactively prevent all drone flights over a utility’s property, their existing authority empowers them to investigate unsafe or illegal drone use. Beyond federal laws, local or state laws may come into play, especially laws that address the following:
- Trespassing on property.
- Disorderly and unsafe conduct.
- Interference with public safety operations.
- Public and harassment laws
Utilities can coordinate with local law enforcement to investigate attacks and deter future drone incursions. Local law enforcement typically has the knowledge to assist utility owners that are reaching out to federal authorities to investigate suspicious drone activity.