TSA has announced that it will be auditing physical security sites that are located in critical energy infrastructure locations. It is expected that in the coming years TSA will release physical security directives regarding site criticality determination, threat and vulnerability assessments, and security countermeasures that will come with compliance requirements and consequences, similar to NERC CIP requirements for electric utilities. A knowledgeable, strategic partner can help utilities prepare for and respond to relevant directives; and should have the experience to evaluate pipeline infrastructure and determine which facilities should be classified as critical and how they can be defended.
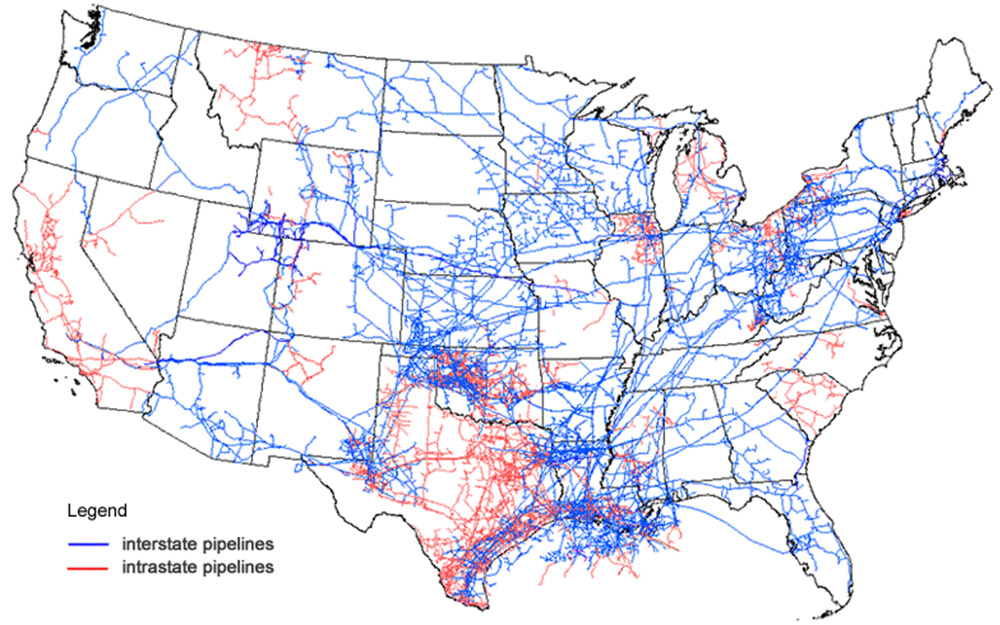
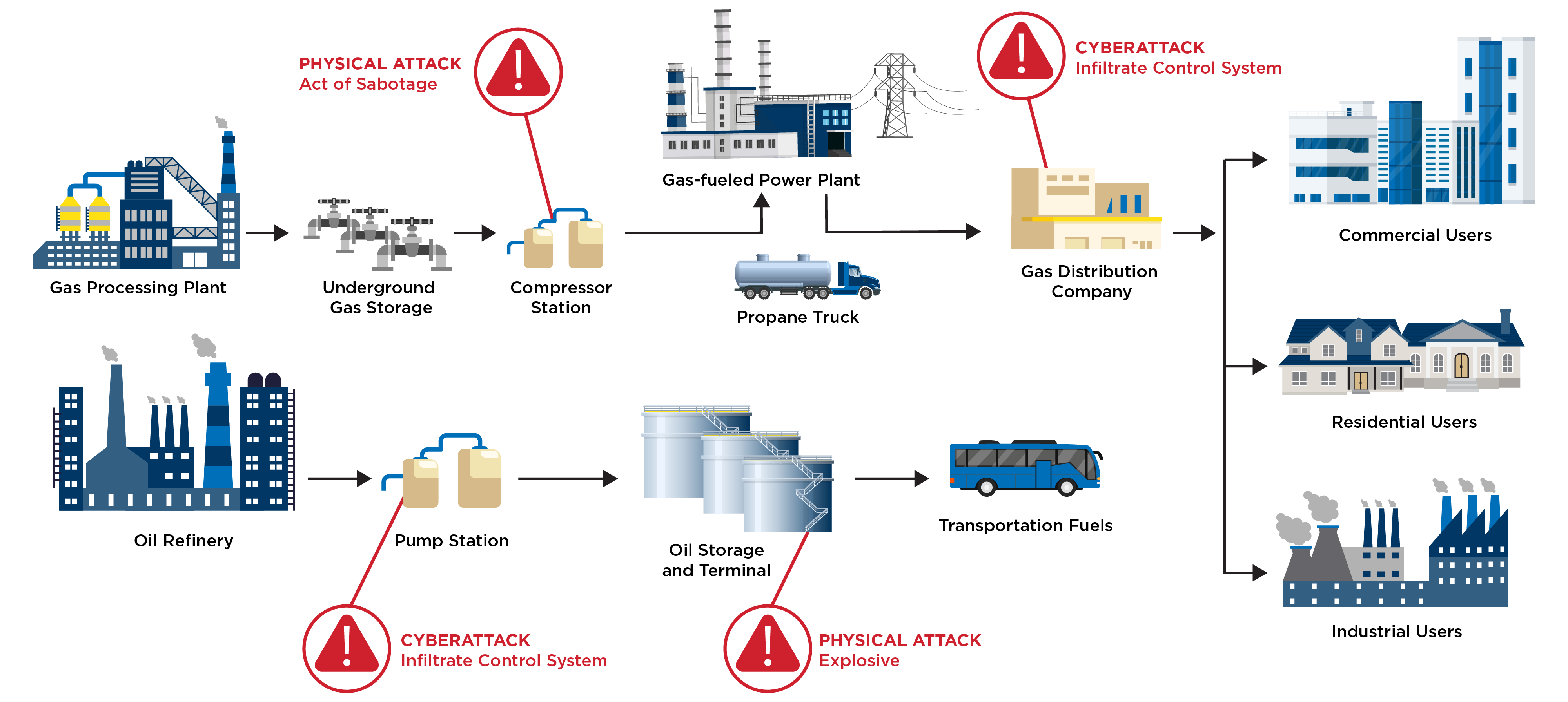
For decades, energy system operators, both gas and electric, have relied on the rural/undeveloped locations of their system assets to be a significant component of their security strategy, best described as out of sight, out of mind. This approach needs to evolve. A more holistic method to mitigate the risk of physical attacks includes layers of security countermeasures such as physical barriers, surveillance systems, intrusion detection and access controls.
Beyond that, utilities can get left of bang through deliberate and thoughtful threat intelligence analysis. Threat monitoring and coordination between law enforcement agencies and private companies will help utilities proactively anticipate, detect and respond to threats of sabotage and other attacks. Lastly, public awareness campaigns are helpful in educating the public about the risks of pipeline attacks and encouraging individuals to report any suspicious activities near critical infrastructure.
Security mitigation measures can come at great cost to pipeline distribution operators. Depending on each state’s public utilities commission, there may be opportunities to include new security measures to existing sites through the rate case process. That said, these projects still must balance the needs of customer affordability, system reliability, safety and security. With each new attack, the need for security considerations to influence these decisions becomes increasingly important.
An experienced team made up of security professionals and pipeline engineers working in-house together to provide consulting for both business-critical infrastructure and critical energy infrastructure as defined by TSA is ideal. A team such as this could seamlessly conduct threat and vulnerability assessments of key facilities, offer risk management consulting, write security standards and policies, and design efficient electronic security systems enterprisewide in an effort to keep important infrastructure assets protected.