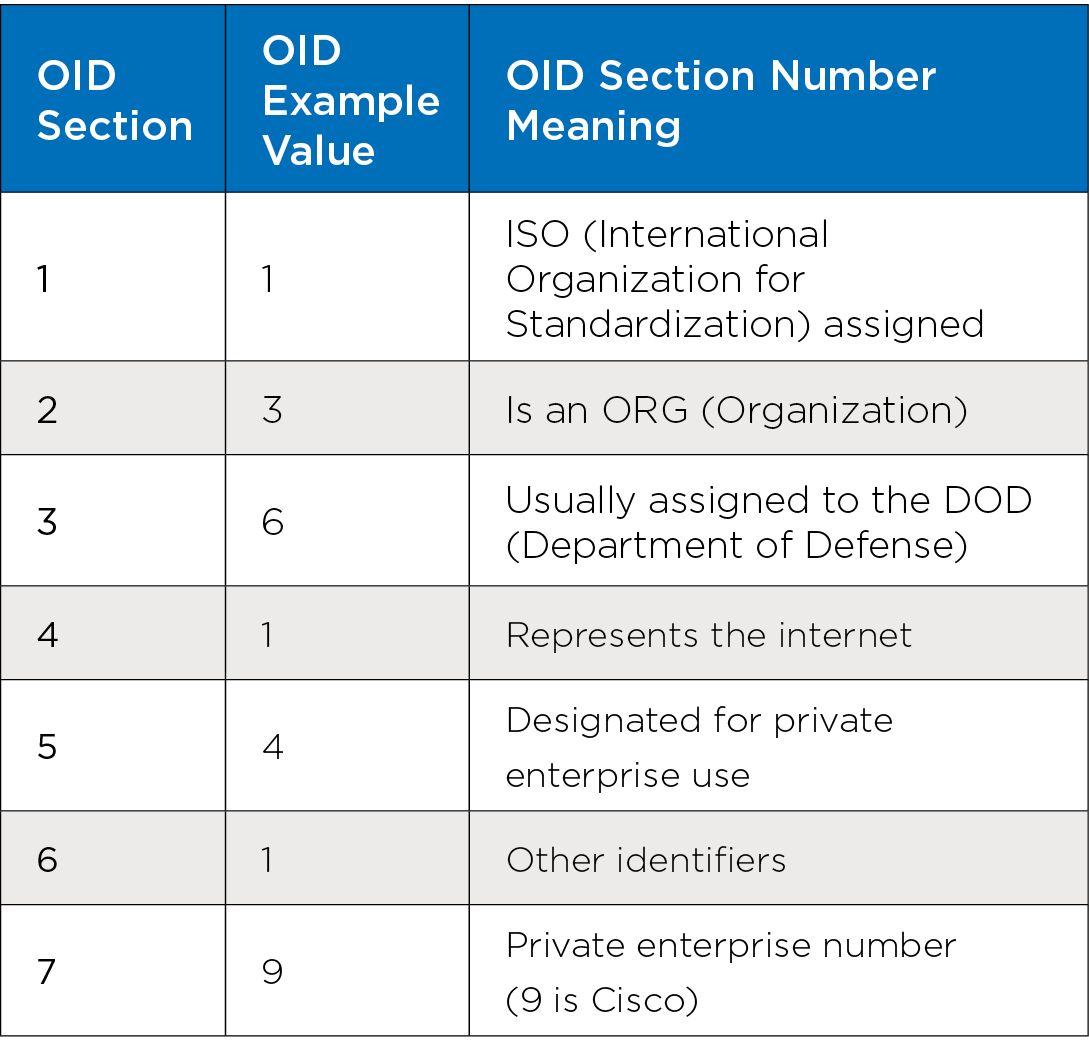
OIDs are assigned more values separated with periods to represent different data points. OIDs are hierarchical and organized in a tree structure for ease of navigation. Each tree level corresponds to a specific group of objects ranging from system settings to the state of protocols or ports. OIDs have different types, such as bits, integers or strings. OIDs are primarily used to monitor and retrieve information from network devices by using the SNMP GET and GETNEXT operations to retrieve current information about the device. Typically, OIDs are read-only, but the SNMP SET operation can configure a device by sending a new value for an OID, and the system will change the setting. However, proper access rights need to be configured to work correctly.
The MIB file for each particular model of equipment is different so it is important to have the vendor MIB for each. It is also important to know that multiple MIB files can be used for one device.
Typically, MIB files are split into different functions. For instance, one MIB file may be for functions shared by the same device class, such as routers with the same features, typical system settings, or hostnames. There are also unique MIB files with a set of OIDs for a particular feature, such as a GPS receiver only available on a specific device.
Making the decision on which type of OID to enable without investigation can result in enabling OIDs that are for features that a utility may not use or miss enabling OIDs that are critical features for network monitoring. Once the MIB files are obtained, OIDs are selected, and they must be classified as enabled and given a severity level.
MIB files can range from just a few OIDs to hundreds. Enabling all alarms could be counterproductive, especially since someone would have to enter them into a trap collector, discussed in more detail below. The next step is to assign each alarm a severity level. A common approach is to classify the alarms as critical, major, or minor. For example, critical alarms are conditions that can cause a communications outage, such as a routing protocol in the “down” state on a router. A loss of redundancy is an example of a major error, assuming the device has a redundant power supply, and there is time to replace the failed unit with no outage. A minor error is an event that needs to be addressed, but will not likely affect the network's operation.
Syslog servers receive information about unauthorized access attempts and information about changes on a system. This information can be critical for finding the root cause of network issues when a network change could be the culprit. Syslog servers receive and store log messages from devices on the network. Log messages contain a time stamp, the host name of the device that sent the message, the severity level, facility and message content. The messages are sent sequentially and can be used as a log for future processing if an event requires security analysis or an audit trail. Real-time processing of syslog messages would offer real-time visibility into the network through a security information and management system; however, these systems may require specific integrations with different devices and are typically not used for condition alarming like SNMP.