Remote access technologies represent a critical innovation, offering unprecedented capabilities for maintaining complex industrial systems. However, these advances come with complex cybersecurity challenges that demand sophisticated, strategic approaches.
Industrial operations have undergone a profound metamorphosis, from manual to automated. Historically, industrial operations relied on manual interventions and on-site technical support. Engineers would travel significant distances, investing significant time and incurring substantial expenses to diagnose and resolve equipment issues.
Modern remote access technologies have dramatically disrupted this paradigm, enabling instantaneous, secure technical interventions that can be conducted from anywhere in the world. Pipelines, airports, water treatment facilities, manufacturing facilities and many more locations have increasingly implemented more automation on their operational technology (OT) networks.
The automation is primarily controlled by programmable logic controllers (PLCs) and interfaced with human-machine interfaces (HMIs). These are immensely flexible platforms that allow a program to automatically run or shut down a process or piece of equipment. PLCs and HMIs have been used for decades to increase production, reduce downtime and respond to a process much faster than a human could. With this increase in use, there has been an increase in complexity and more overlap with cybersecurity concerns.
The building and installation of new equipment at a facility can require installing new PLCs and HMIs or integrating the new equipment into the existing PLCs and HMIs. Most of the time, this is done by a subcontractor with little to no technical interaction with the facility owner. Once the project is complete and the equipment has been commissioned, the owner is responsible for the new system.
When equipment is replaced, or instruments need to be replaced, or a process is modified, the owner will need to engage the subcontractor(s) that installed the system. Sometimes, the original contractor cannot help with the modifications after the initial installation. An owner may need to hire a local integration contractor for the modifications to the control system. The install subcontractor(s) will receive specifications for the modifications and be physically present on-site for a field visit and later for implementation.
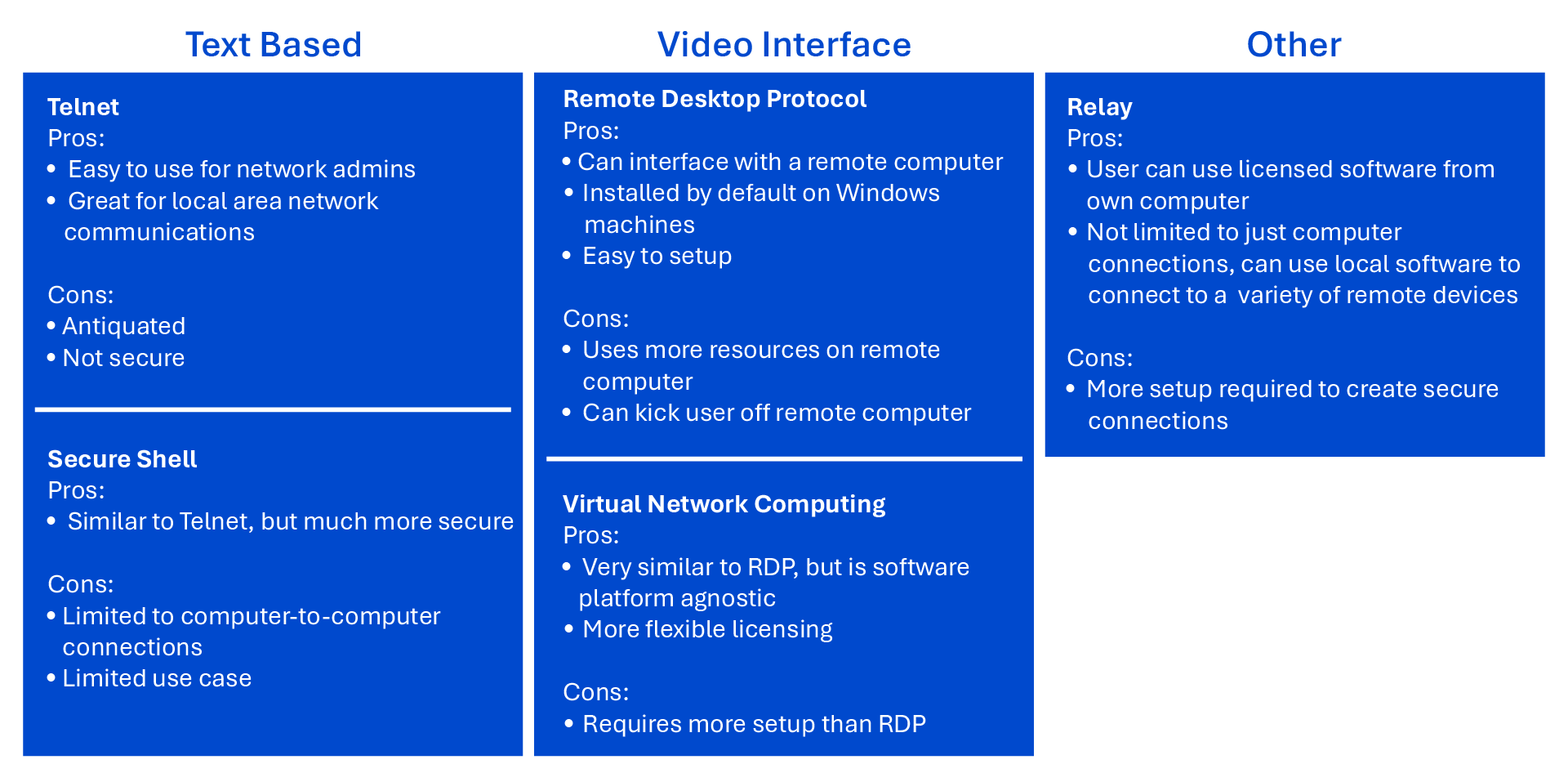
If there are continual changes, the install subcontractor may have a service contract. Difficulties can include scheduling, availability and travel issues. One of the easiest ways to alleviate these issues is to grant the subcontractor remote access to the site. This would allow remote resources to connect to the OT controls network, with assistance from local operators, and work can be completed without needing a physical resource on-site.
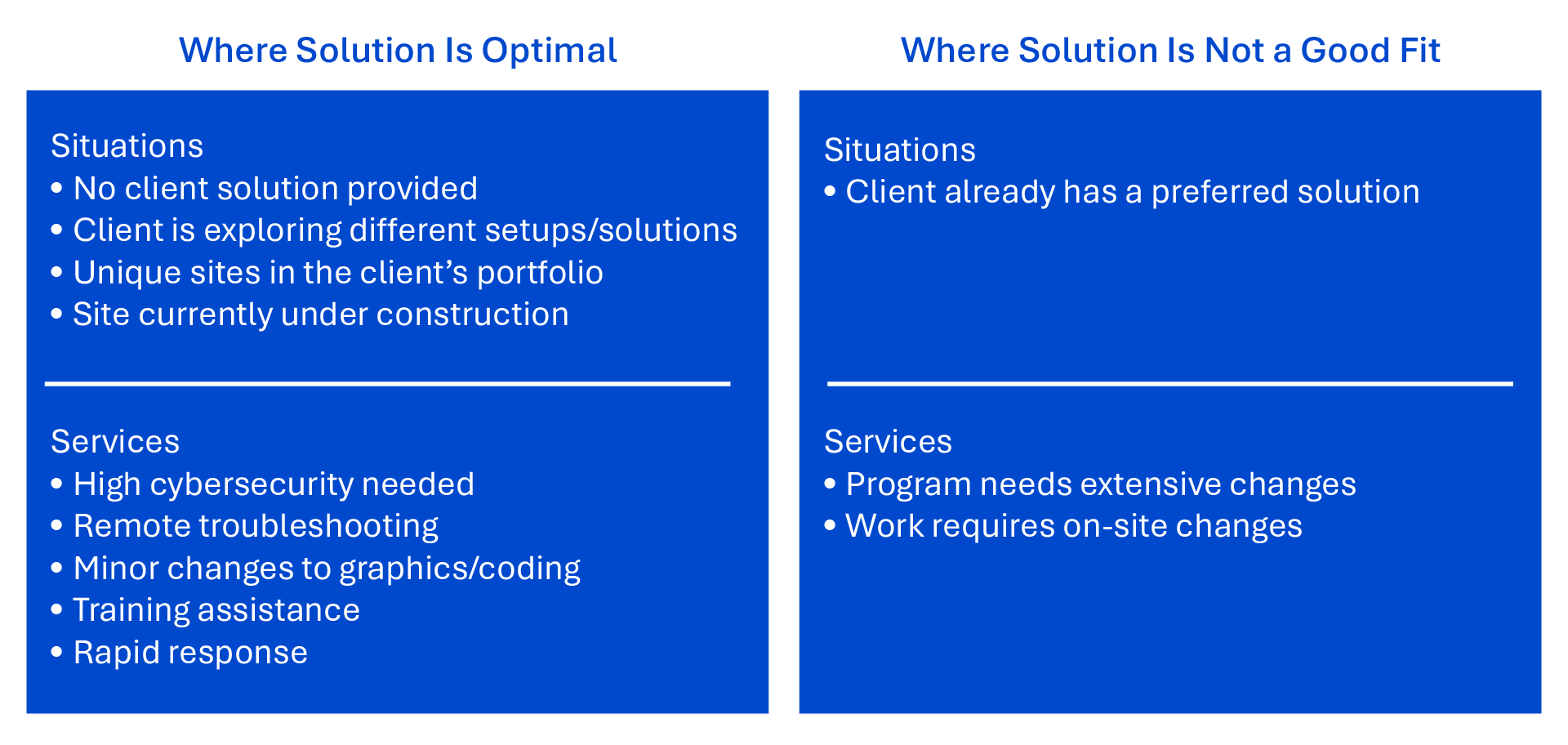
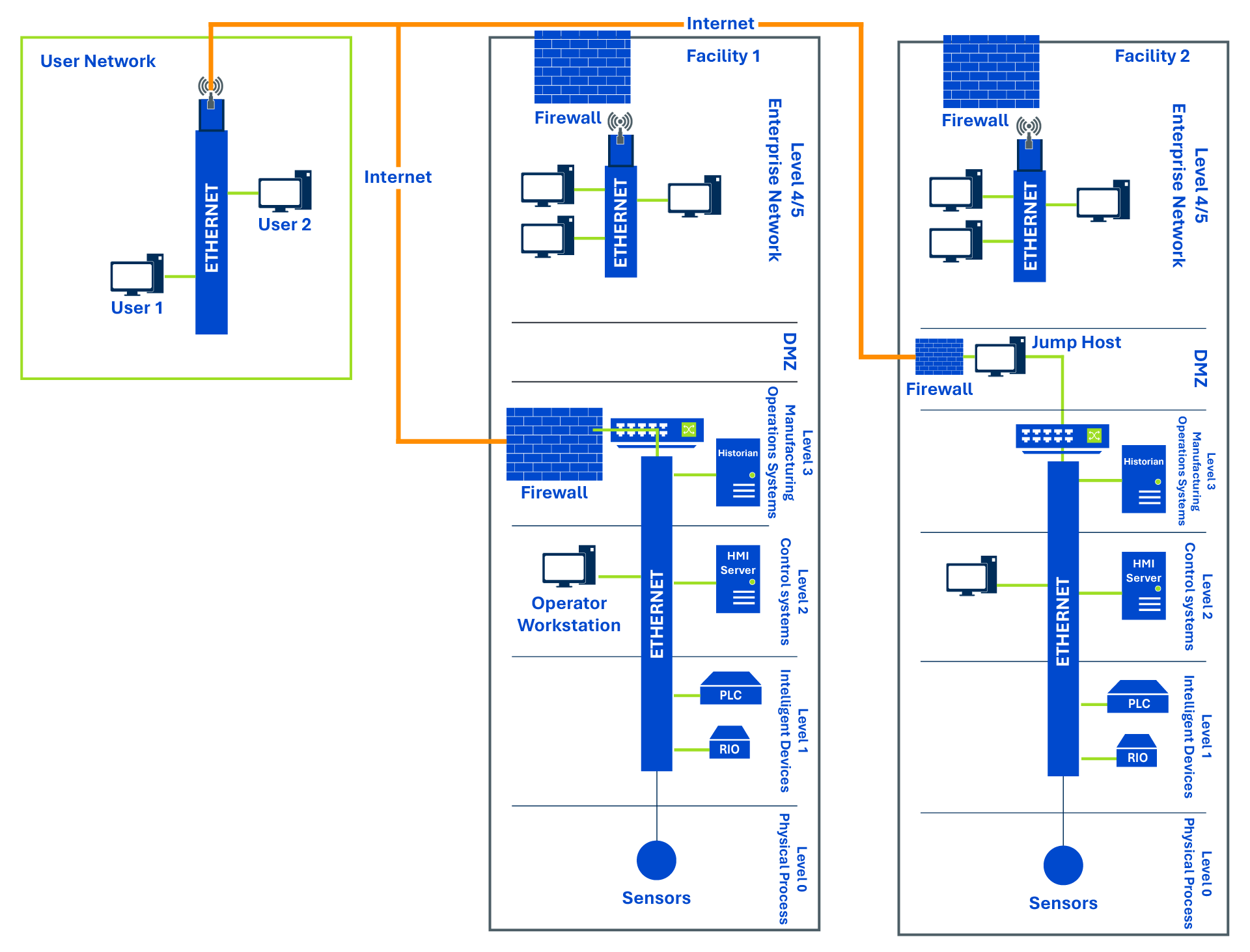
But what happens if a client site wants to use a product that requires continual outside access (software as a service, remote dashboards, AI analytics, etc.)? How will that third-party be able to safely access information from the site? Figure 1 shows examples of where remote access is needed, even if it is one-directional.