The security team at Burns & McDonnell has conducted hundreds of assessments across the country and often sees faulty approaches to security planning. Among the most common:
- The reactive approach chooses security based on past security incidents alone. This is an impulsive response that tries to see that a recent attack doesn’t happen again. However, not considering the root cause of such incidents and other risks leaves assets vulnerable.
- The get-what-you-pay-for approach assumes that spending a lot of money on the latest technology equals reduced risk. Sadly, hundreds of thousands of dollars of security resources have been wasted this way.
- The piecemeal approach tries to address security without an overall strategy or plan. We often see this at older facilities that have been pieced together over the years.
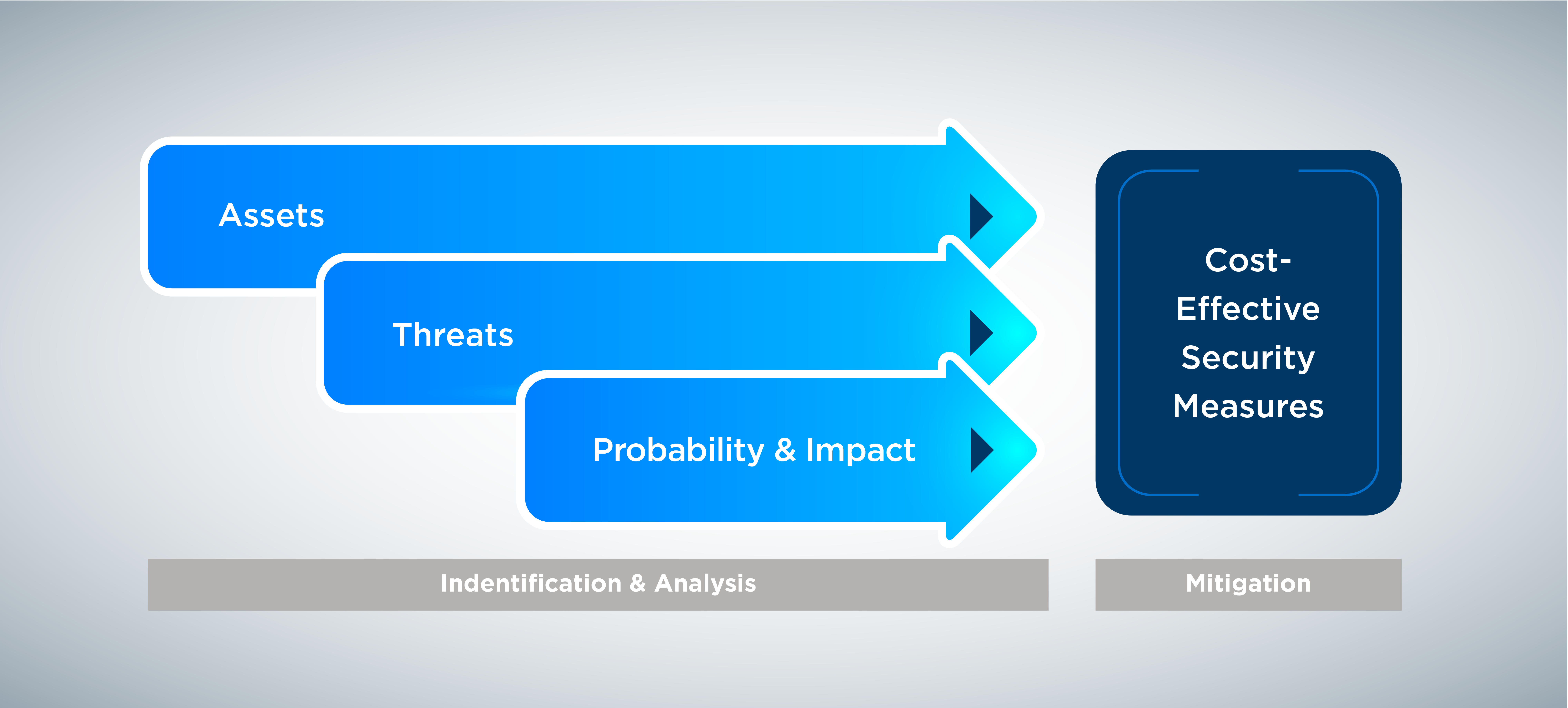
The better solution is a risk-based approach. This may take more work upfront but yields improved security for less money. The risk-based approach is a systematic analysis of the underlying risk factors to determine where security is needed most. This approach evaluates frequency and impact of adverse threat events on identified company assets.
The result of this analysis shows what assets are vulnerable and what security countermeasures are cost-effective. Identifying key assets is a commonly overlooked first step but it is foundational for security planning. One of the key benefits of a risk-based approach is that the true cost of an attack is quantified in terms of dollars. Costs can include lost production, lost reputation and lost business. Once the cost of an attack is quantified, it can easily be compared to the cost of security countermeasures to reveal which countermeasures are cost-effective. In this way, owners can be confident that they are not overspending on security and that they have reasonable security in place. Applying a risk-based approach and industry-recognized security principles can help clients identify security-related threats, mitigate vulnerabilities and manage risk.