Service Feature
Security Services for Critical Infrastructure
BY Landon Jones and Jared Oakden
Countless people depend on critical infrastructure every day for safe and reliable service. Owners and operators are prioritizing the physical security of their critical infrastructure with the ultimate objective of improving safety and resiliency.

When considering security upgrades, owners and operators of critical infrastructure often wonder what minimum security should be in place and if the current state of their security is adequate. Understanding immediate needs to address urgent vulnerabilities is a first step toward optimal security.
Regardless of your industry or facility size, type or location, we provide security assessments, security management consulting and security design services that take into account your distinctive characteristics and needs. We want you to reduce vulnerabilities while optimizing your investments, so you can provide quality service and maintain safe operations.
Security recommendations are based on each client’s unique risks and the most cost-effective way to mitigate vulnerabilities. Burns & McDonnell is committed to helping critical infrastructure owners make wise investments and ultimately keep people safe for years to come.
Security Assessment Service
Owners and operators are reexamining their security needs and looking for a more comprehensive understanding of the physical security needed for their critical infrastructure. Our security assessments help clients understand their security needs and whether their existing security is adequate. Effective security requires the right combination of people, policies and procedures, and countermeasures — such as cameras, fences and gates. During a security assessment, we’ll compare your security to current industry best practices while identifying potential vulnerabilities and threats. The resulting analysis helps support the business case for investing in security while providing maximum effectiveness for every dollar spent.
Security assessment services include:
- Assessing overall security program effectiveness.
- Evaluating the threat environment.
- Assessing security vulnerability.
- Identifying and analyzing threats to assets.
- Recommending security countermeasures to protect assets.
- Using Crime Prevention Through Environmental Design (CPTED).
- Conducting line-of-site study for ballistic attacks.
Security Management Consulting
The most effective security programs are backed by a comprehensive strategy. An effective strategy incorporates electronic security, training and employee awareness, emergency response planning, regulatory compliance, and budget management. Without a plan, owners and operators of critical infrastructure may struggle to budget for future upgrades and expenses. We’ve developed security master plans for numerous clients across the U.S. By creating and following long-term plans for a security program, you are taking the necessary steps to improve over time while mitigating risks.
Security management consulting services include:
- Regulatory compliance planning.
- Risk management strategy.
- Security master planning.
- Development of staffing plans.
- Prioritized short- and long-term plans for security upgrades.
- Security operations center (SOC) planning.
- Writing policies and procedures.
- Employee security training.
- Phased approach to security program maturity.
Regulatory compliance is a constant concern for critical infrastructure operators. We help clients apply physical security related regulations and guidelines issued by the following organizations:
- North American Electric Reliability Corporation (NERC).
- Federal Energy Regulatory Commission (FERC).
- Transportation Security Administration (TSA).
- Environmental Protection Agency (EPA).
- Cybersecurity and Infrastructure Security Agency (CISA).
- Department of Energy (DOE).
- Department of Defense (DOD).
Security System Design
Security system design is the process of establishing the technical details of electronic security systems, including the types of cameras, the exact placements of cameras and the fields of view. These details will ultimately determine if a system is cost-effective and functions as intended. We routinely design security systems for critical infrastructure, utilities, airports, and state and federal government clients. This service provides detailed security specs and drawings of all electronic security devices and their connections to the larger information technology infrastructure. Clients who use our design services can rely on a well-designed system that will last years, cost less and provide security as intended.
Security system design services include:
- Vendor-agnostic recommendations for modernizing or replacing existing security systems.
- Security design standards.
- Camera system design.
- Card reader system design.
- Intrusion alarm system design.
- Fences and gates design.
- Blast hardening design.
- Requests for proposal bid support.
- Owner’s rep services.
- Commissioning services.
- Design drawings and specs for installation.
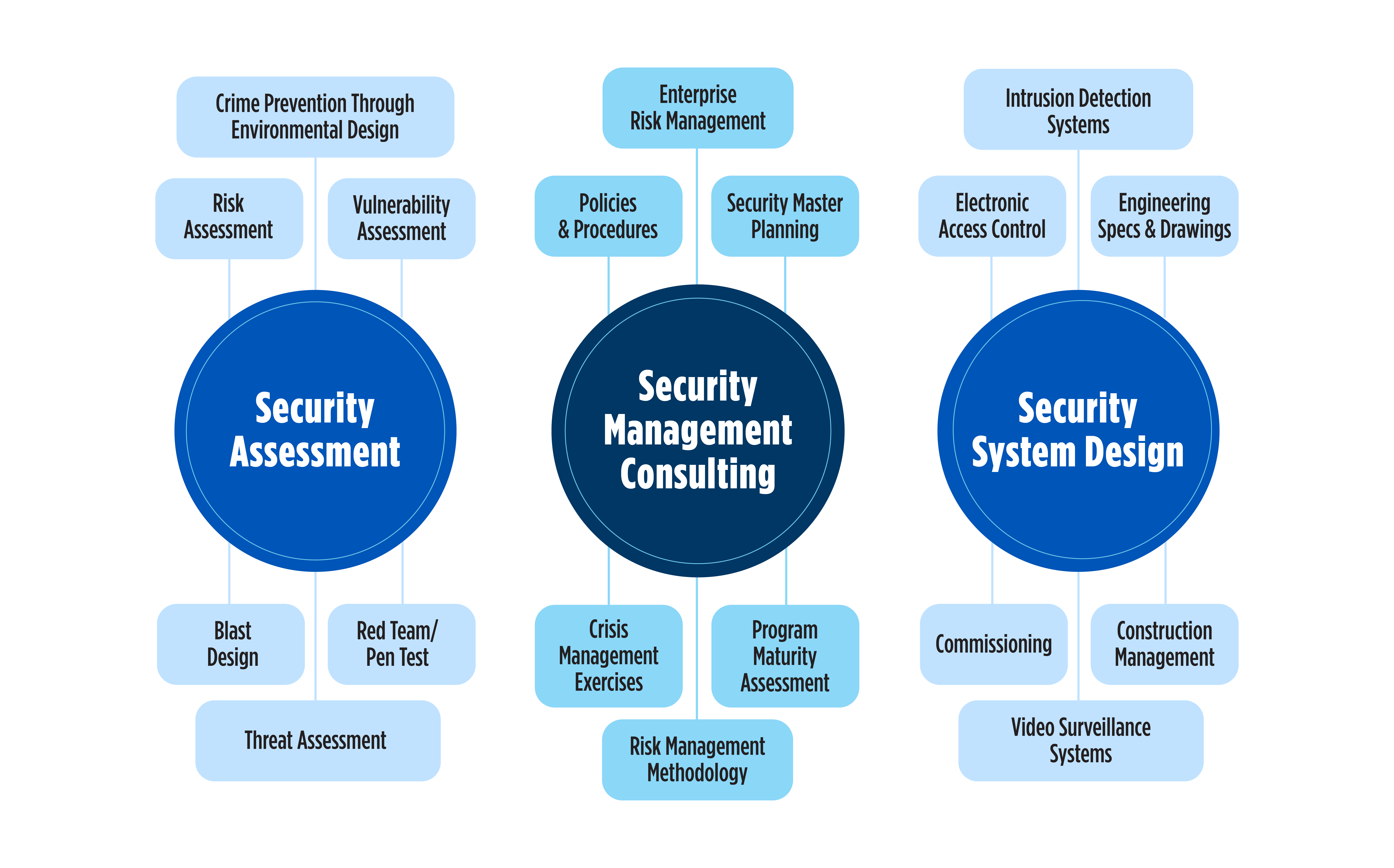
Figure 1: Security services for critical infrastructure.
Burns & McDonnell understands the goal for critical infrastructure is zero service interruptions. By offering security assessments, security management consulting and security system design services, we can help you avoid disruptions caused by security incidents.
As an independent adviser, we’ll investigate each unique challenge before identifying a solution. At the start of the project, you’ll meet with a consultant who will create a project plan and work with you to improve security, increase reliability and keep people safe.
As an engineering, architecture and construction company, Burns & McDonnell designs and builds the critical infrastructure that helps our clients and communities thrive. This experience provides a deep understanding of risks, vulnerabilities and how to protect critical assets. We leverage our experience across many industries to provide creative solutions for the most challenging security problems.
✖