Special Flooring
The floor of a SCIF should be designed with weight limits, access points and nearby neighbors all kept in mind. Design must accommodate any heating/cooling or electrical upgrades that might also be needed to keep a SCIF up to code.
Feature | July 20, 2024
Keeping Espionage at Bay: Protecting Sensitive Info With SCIFs
From a tent sitting amid intense warfare in a balmy desert to the middle of a brightly lit office room in a bustling downtown city, sensitive compartmented information facilities (SCIFs) can essentially be anywhere — because classified information can be anywhere. In an era where knowledge is power, the necessity to safeguard sensitive data has never been more critical.
SCIFs are at the forefront of protecting classified and proprietary information. These highly secure environments are designed with detailed precision and are increasingly being employed in the military and certain commercial industries, particularly in areas involving government or defense-related work.
SCIFs require robust security measures that can vary widely from organization to organization. These can range from safeguarding classified projects to protecting sensitive communication systems. Any information related to national security or possessing national sensitivity can be protected through the use of a SCIF.
Originally developed to prevent spies from gathering sensitive data, SCIFs are intrusion-resistant spaces that keep classified information secure from unauthorized access and espionage. However, as industries such as aerospace and defense contractors increasingly handle sensitive data, the principles behind military-grade SCIFs also translate to many different sectors. This expansion underscores the growing importance of protecting proprietary information, from intellectual property to strategic business plans.
“There is a tremendous amount of industrial and government espionage going on that isn’t discussed or made public,” says David Findlay, associate architect at Burns & McDonnell. “It’s getting more and more complex to protect the info that you need to protect.”
Defense contractors and aerospace companies often require this type of high-level security for warehouses and for other facilities. Because commercial developers may lack detailed understanding of SCIF requirements and features, costly redesigns can be avoided by involving security specialists early in the planning phase of such assets.
The Anatomy of a SCIF
Designing a SCIF is a complex task that requires careful planning and collaboration among various disciplines. Engineers and security specialists must think through every aspect, from the shape of the building to the placement of heating, ventilation and air conditioning (HVAC) ducts and penetrations.
The need for transient electromagnetic pulse emanation standard (TEMPEST) measures further complicates the design. These measures see that electronic emissions are either contained within the SCIF or blocked from entering, with the intent of preventing data breaches. This is especially challenging in spaces such as scientific laboratories that have secure servers or computer systems.
As technology evolves, so do the threats to information security. Modern SCIFs must guard against sophisticated espionage tactics, including the use of artificial intelligence and advanced hacking techniques. The ever-present threat of industrial and governmental espionage adds to the urgency of developing robust security measures.
One significant challenge is the potential threat posed by modern communication devices. For example, smartphones have continued to boost their capacity for capturing information. Drones also introduce an increased security risk. Such complexities require constant vigilance and innovation in SCIF design and implementation.
“The complexities of designing a SCIF are astounding,” says Betsy M. Perry, senior associate architect at Burns & McDonnell. “Our teams are constantly thinking of innovative solutions when they run into unique situations within the development stage of a SCIF.”
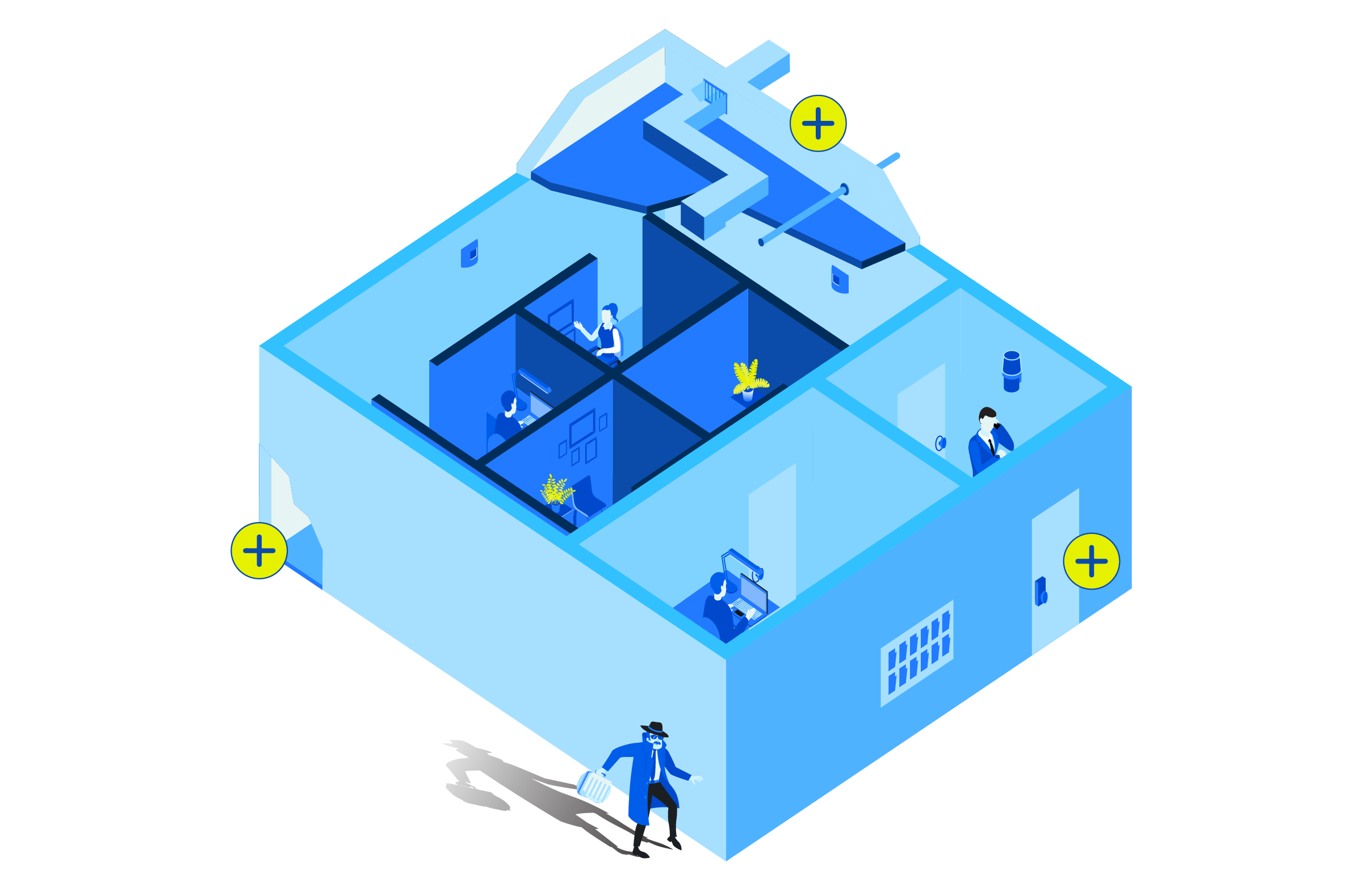

The floor of a SCIF should be designed with weight limits, access points and nearby neighbors all kept in mind. Design must accommodate any heating/cooling or electrical upgrades that might also be needed to keep a SCIF up to code.
SCIF walls have specific modifications to prevent physical access into the facility, including altered heating/cooling systems, motion sensors and no windows built into the room. The walls are also designed to stop sound from entering or leaving the facility to obstruct information from being obtained.
One of the more obvious security checkpoints, the door leading into a SCIF that serves as the main entrance is often secured with a spin dial lock and card reader. The locking hardware must meet Federal Specification FF-L 2740 and requires a two-factor authentication to be able to enter the room.

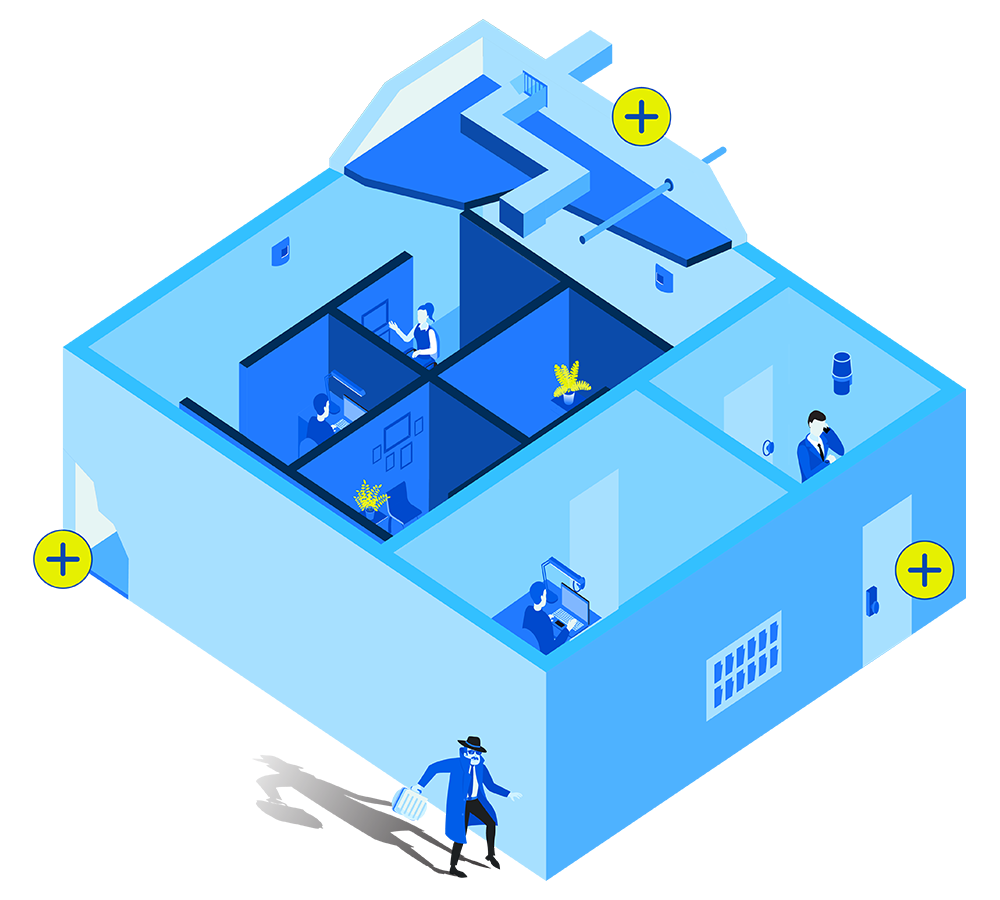

The floor of a SCIF should be designed with weight limits, access points and nearby neighbors all kept in mind. Design must accommodate any heating/cooling or electrical upgrades that might also be needed to keep a SCIF up to code.
SCIF walls have specific modifications to prevent physical access into the facility, including altered heating/cooling systems, motion sensors and no windows built into the room. The walls are also designed to stop sound from entering or leaving the facility to obstruct information from being obtained.
One of the more obvious security checkpoints, the door leading into a SCIF that serves as the main entrance is often secured with a spin dial lock and card reader. The locking hardware must meet Federal Specification FF-L 2740 and requires a two-factor authentication to be able to enter the room.

A SCIF can vary in size and complexity, ranging from a simple closet to a dedicated room within a facility to a full-scale building complex. The fundamental design requirement to be accredited as a SCIF is a six-sided secure space comprising four walls, with a solid ceiling and floor. Security extends beyond the physical structure, often involving a multilayered approach that includes perimeter fencing, security personnel and multiple access control points before reaching the SCIF itself.
“There is a tremendous amount of industrial and government espionage going on that isn’t discussed or made publicly known. It’s getting more and more complex to protect the info that you need to protect.”
David Findlay, Associate Architect Associate Architect
The White House War Room is probably the most well-known and commonly thought of SCIF. This room is designed for people to discuss sensitive information and make crucial decisions that could impact the national security of the U.S. However, most SCIFs aren’t nearly as famous. SCIFs can be found within the walls of hotels built for traveling national security officials or in private residences. Many U.S. presidents have been known to have SCIFs in their personal homes to discuss information that has the potential to influence the fate of national security.
While SCIFs can be found in many different locations, all SCIFs must be designed according to rigorous standards and be accredited and formally approved by a regulating agency. To meet the required Sound Transmission Class rating, additional layers of drywall, insulation or concrete may need to be added to the space to prevent signals from being transmitted in and out of the secured room. Additionally, the existing room may need to be reconfigured and stripped down to the bare walls and ceilings to allow for a redesign.
Accrediting officials, site security managers and certified TEMPEST technical authorities play major roles in SCIF projects. They work together to determine the necessary security threshold — addressing concerns such as physical and acoustical security, implementing intrusion detection systems (IDS), and incorporating TEMPEST measures.
The meticulous design, stringent security measures and evolving technologies that underpin SCIFs are essential in safeguarding the information that drives our world forward. As threats continue to evolve, so too must strategies for maintaining the integrity and confidentiality of the most sensitive and valuable data.
Related Content
Blog
Key Reasons Behind the Growing Demand for SCIFs
What We Do
Industrial Cybersecurity
Aerospace
Redefining What’s Possible With Innovative Aerospace, Defense & Space Facilities


.png)
BenchMark is an international award-winning news source published by Burns & McDonnell. Since 1926, it has served as an innovative, forward-thinking and solutions-driven resource for communities and industries around the world.
©2026 Burns & McDonnell All Rights Reserved.